GIAC Certified Incident Handler (GCIH): GCIH
Want to pass your GIAC Certified Incident Handler (GCIH) GCIH exam in the very first attempt? Try Pass2lead! It is equally effective for both starters and IT professionals.
- Vendor: GIAC
- Exam Code: GCIH
- Exam Name: GIAC Certified Incident Handler (GCIH)
- Certifications: GIAC Certifications
- Total Questions: 705 Q&As( View Details)
- Updated on: Aug 10, 2025
- Note: Product instant download. Please sign in and click My account to download your product.

- Q&As Identical to the VCE Product
- Windows, Mac, Linux, Mobile Phone
- Printable PDF without Watermark
- Instant Download Access
- Download Free PDF Demo
- Includes 365 Days of Free Updates
VCE
- Q&As Identical to the PDF Product
- Windows Only
- Simulates a Real Exam Environment
- Review Test History and Performance
- Instant Download Access
- Includes 365 Days of Free Updates
Passing Certification Exams Made Easy
Everything you need prepare and quickly pass the tough certification exams the first time
- 99.5% pass rate
- 7 Years experience
- 7000+ IT Exam Q&As
- 70000+ satisfied customers
- 365 days Free Update
- 3 days of preparation before your test
- 100% Safe shopping experience
- 24/7 Support
GIAC GCIH Last Month Results
Free GCIH Exam Questions in PDF Format
Related GIAC Certifications Exams
GCIH Online Practice Questions and Answers
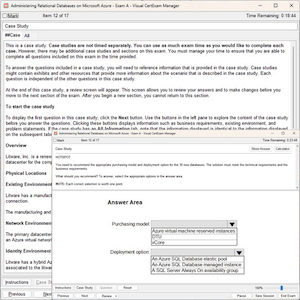
Questions 1
Which of the following functions can be used as a countermeasure to a Shell Injection attack? Each correct answer represents a complete solution. (Choose all that apply.)
A. escapeshellarg()
B. mysql_real_escape_string()
C. regenerateid()
D. escapeshellcmd()
Questions 2
An analyst ran a Nessus scan with Dangerous plugins enabled for performing a vulnerability scan against a business critical system running on the production network. This brought down the target host, without alerting on it while the scan was occurring. How could the scan have avoided crashing the target host?
A. Never scan production networks, since they are business critical at all times
B. Scan the business critical systems, after you disable dangerous plugins
C. Do not scan any business critical systems, since they have other priorities
D. Use a different vulnerability scanner, since Nessus is dangerous in this situation
Questions 3
Where would an incident handler search for autostart extensibility points (ASEPs) on a Windows host?
A. Firewall configuration control panel
B. Local machine registry hive
C. Windows Temp Directory
D. Security event logs
Reviews
-
i'm very happy that i passed the exam successfully. Recommend.
-
took the exams yesterday and scored 9xx.dumps are valid. almost all of the multiple choice came out. I advice know ur material very well and then U can read dumps. good success
-
This dumps is valid, and this dumps is the only study material i used for this exam. Surprisingly i met the same question in the exam, so i passed the exam without doubt. Thanks for this dumps and i will recommend it to my friends.
-
Answers are correct. Questions are valid.Recommend strongly.
-
The answers are accurate. Well you should notice some of the questions are slightly changed. Be careful.
-
Thanks god and thank you all. 100% valid. all the other questions are included in this file.
-
Thanks for your help. I passed my exam yesterday with a high score. I think you have the great dumps. all my questions are from your materials. I'm very happy with that. Thanks.
-
I'm so glad that I have chosen you as my assistant with my exam. I passed my exam. Full scored. I will recommend to friends.
-
Dump valid! Only 3 new questions but they are easy.
-
took the exams yesterday and passed. I was very scared at first because the labs came in first so I was spending like 10 to 13mins so I started rushing after the first three labs thinking that I will have more labs. I ended up finishing the exam in an hour..d dumps are valid. I tink there is a new lab. good success


 Printable PDF
Printable PDF